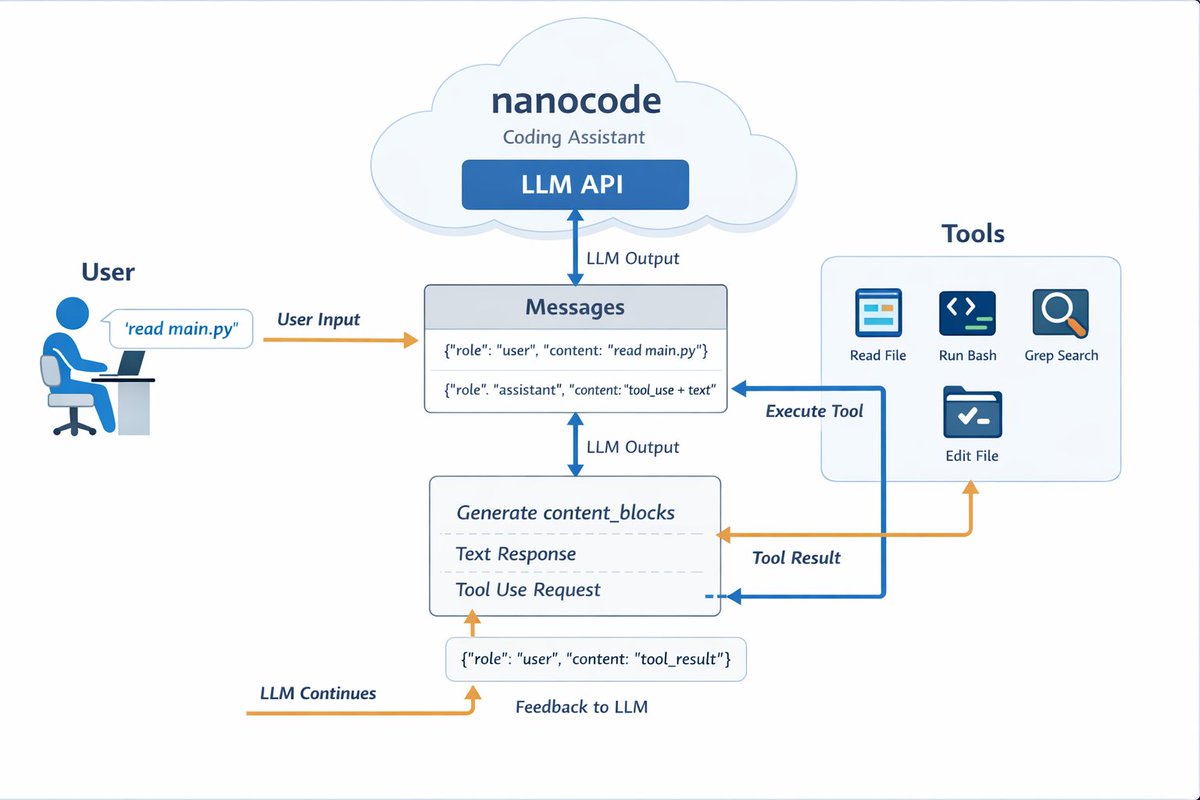
RoboParty has fully open-sourced its bipedal humanoid robot technology stack (including hardware, control, training, and deployment) on GitHub.
Price Converter
- Crypto
- Fiat
USDUnited States Dollar
CNYChinese Yuan
JPYJapanese Yen
HKDHong Kong Dollar
THBThai Baht
GBPBritish Pound
EUREuro
AUDAustralian Dollar
TWDNew Taiwan Dollar
KRWSouth Korean Won
PHPPhilippine Peso
AEDUAE Dirham
CADCanadian Dollar
MYRMalaysian Ringgit
MOPMacanese Pataca
NZDNew Zealand Dollar
CHFSwiss Franc
CZKCzech Koruna
DKKDanish Krone
IDRIndonesian Rupiah
LKRSri Lankan Rupee
NOKNorwegian Krone
QARQatari Riyal
RUBRussian Ruble
SGDSingapore Dollar
SEKSwedish Krona
VNDVietnamese Dong
ZARSouth African Rand
No more data