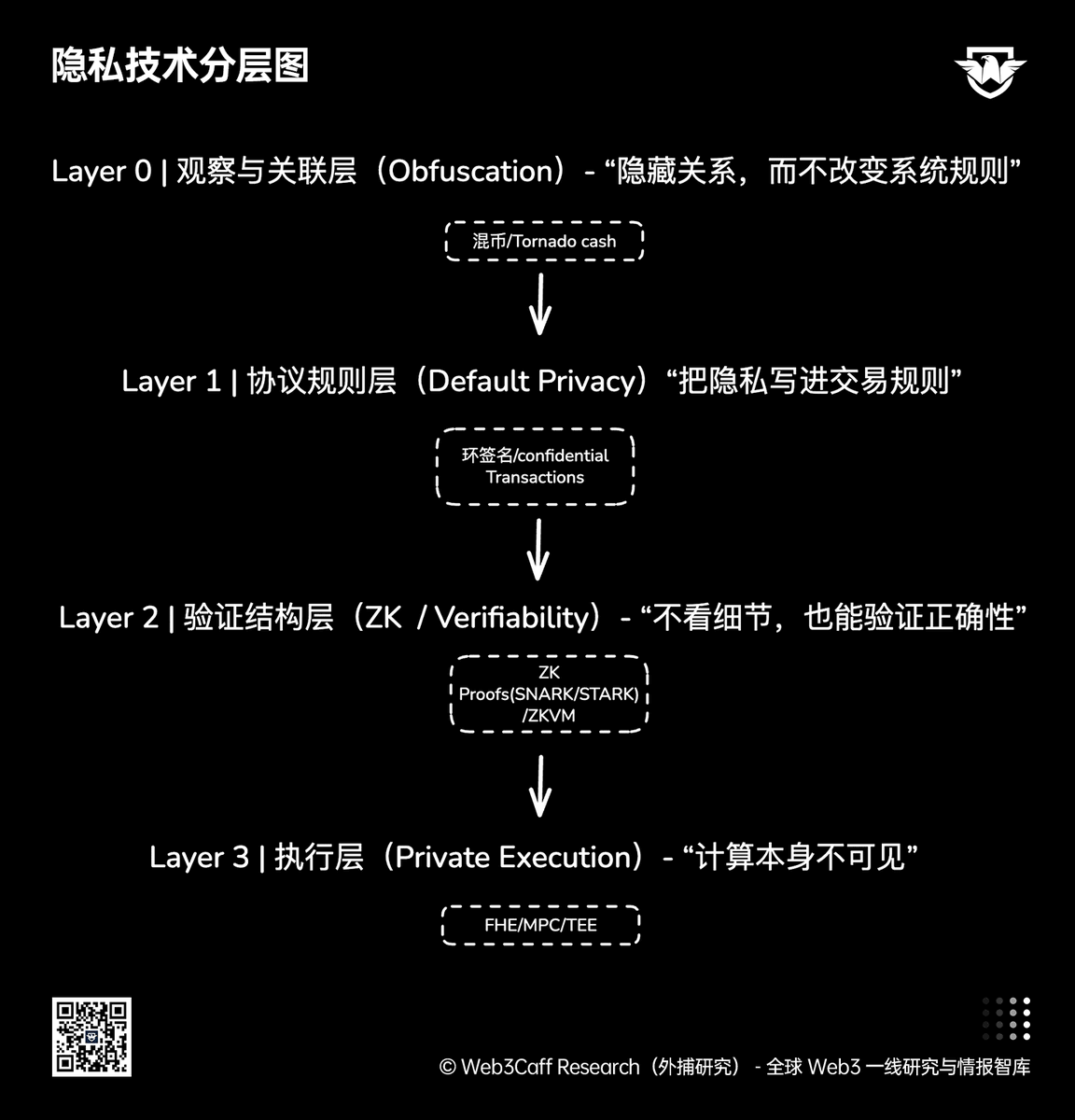
Blockchain privacy technology has gradually evolved from "hiding observable relationships" to "changing the verification structure," and finally to a stage where "execution itself is invisible." The diagram below illustrates a technology map categorized by privacy levels to provide a unified understanding of the core problems addressed by different privacy solutions.
The topmost observation and association layer weakens external analysis capabilities by obfuscating transaction paths or address relationships, but it doesn't change the system's execution and verification logic. Its privacy strength depends on the size of the anonymity set and user behavior, making it difficult to provide verifiable guarantees.
Further down to the protocol rule layer, privacy is directly written into transaction and ledger rules, making anonymity a default attribute. This type of solution provides stable and enforced privacy protection, but often sacrifices composability, ecosystem scalability, and compliance flexibility.
The verification structure layer reconstructs the system's trust mechanism through zero-knowledge proofs, allowing nodes to verify the correctness of state transitions without reproducing execution details, thus achieving, for the first time in a public system, the coexistence of "verifiability" and "detail hiding."
The lowest-level execution layer privacy further challenges traditional computing premises: through FHE, MPC, or TEE, computation is completed without exposing plaintext, addressing the privacy issue of "data in use." This layer typically does not exist alone but is combined with ZK to form a complete private execution and verification system.
This layered structure does not imply that technologies are mutually replaceable, but rather reveals the position and boundaries of different privacy solutions within the system stack. Real-world systems are often combinations of multiple technologies, rather than the result of a single privacy tool.
The above content is excerpted from Web3Caff Research's "Privacy Infrastructure Track 26,000-Word Research Report: Under the Global Compliance Wave, How Is Privacy Reshaping the Web3 Underlying Paradigm? From the Evolution of Four Generations of Privacy Technologies, to the Differentiation of ZK/FHE/TEE Routes, Compliance Architecture Choices, Ecosystem Status, and Evolution Trends in the Next Decade"
Click to view the full version 👇